
Overview
- Phish Tale of the Week
- Microsoft’s BlueKeep Proves Vulnerable
- Critical Warning Issued for Samsung Cellphone Update App
- How Can Netizen Help?
Phish Tale of the Week
Phishing attempts are often carried out with urgent messages that are meant to provoke the victim to act without rationally thinking about the contents of the email. In this instance, an employee received an email message from their boss asking them to buy Amazon gift cards for his best friend’s son’s birthday.
Take a look below:

- The first tell-tale sign is the “boss” emailing the employee for a personal favor, and asking for it urgently.
- A second attempt at urging the victim to act quickly and ignore rational thinking.
- Improper grammar is used throughout the email, including the highlighted line.
- A very shady way of loading money onto a gift card is being requested, further raising suspicions.
General Recommendations:
A phishing email will typically direct the user to visit a website where they are asked to update personal information, such as a password, credit card, social security, or bank account information. A legitimate company already has this sensitive information and would not ask for it again, especially via email.
- Scrutinize your emails before clicking anything. Did you order, or ask for, anything for which you’re expecting a confirmation? Did the email come from a store you don’t usually order supplies from or a service you don’t use? If so, it’s probably a phishing attempt.
- Verify that the sender is actually from the company sending the message.
- Did you receive a message or email from someone you don’t recognize? Are they asking you to sign into a website to give Personally Identifiable Information (PII) such as credit card numbers, social security number, etc. A legitimate company will never ask for PII via instant message or email—this is a huge red flag.
- Do not give out personal or company information.
- Review both signature and salutation.
- Do not click on attachments.
- Do not click on unrecognized links. If you do proceed, verify that the URL is the correct one for the company/service and it has the proper security in place, such as HTTPS.
- Be wary of poor spelling, grammar, and formatting. As can be seen with the with this email, there are multiple spelling, grammar, and formatting errors, leading us to believe that the message is illegitimate. If an email is visually unprofessional, the sender is likely not who they say they are.
Many phishing emails pose a sense of urgency or even aggressiveness to prompt a form of intimidation. Any email requesting immediate action or that is addressing you in a threatening manner should be questionable. Also, beware of messages that seek to tempt users into opening an attachment or visiting a link. For example, an attachment titled “Staff Pay Raises 2019” may seem like something you really want to know about, but it could just be a ploy to plant malware on your system or steal your credentials.
Cybersecurity Brief
In this week’s Cybersecurity Brief: Microsoft’s BlueKeep Vulnerability Proved Exploitable, Critical Warning for Scam Samsung Update App
Microsoft’s BlueKeep Proves Vulnerable

Late last month, Microsoft’s Security Response Team (MSRC) issued a warning to organizations to update and install patches to BlueKeep (CVE-2019-0708), a critical remote code execution vulnerability it patched in early June. The flaw, which affects older versions of Windows and is found in Remote Desktop Protocol (RDP), allows attackers to execute code remotely on a machine without the need to log in. The flaw requires no user interaction, a feature that’s caused concern for future malware which can be developed to exploit the bug and spread the malware across other vulnerable machines. Initially, when the patch was released on May 14, Microsoft had not seen the BlueKeep bug exploited in the wild. However, Microsoft acknowledged that it is “highly likely” that this bug can be exploited by malicious actors and cybercriminals.
Now, almost two months later, BlueKeep discoverer and security researcher Kevin Beaumont stated that there are over a million systems on the internet with RDP exposed publicly and, to underscore the importance of applying Microsoft’s patch as soon as possible, Sophos also released a proof of concept video showing BlueKeep being exploited. This dashed the hope that the difficulty in executing the code would slowdown potential exploitation by criminals. The good news is that there is no evidence of BlueKeep being exploited in the wild.
To read more about the BlueKeep vulnerability, click here.
Critical Warning Issued for Samsung Cellphone App
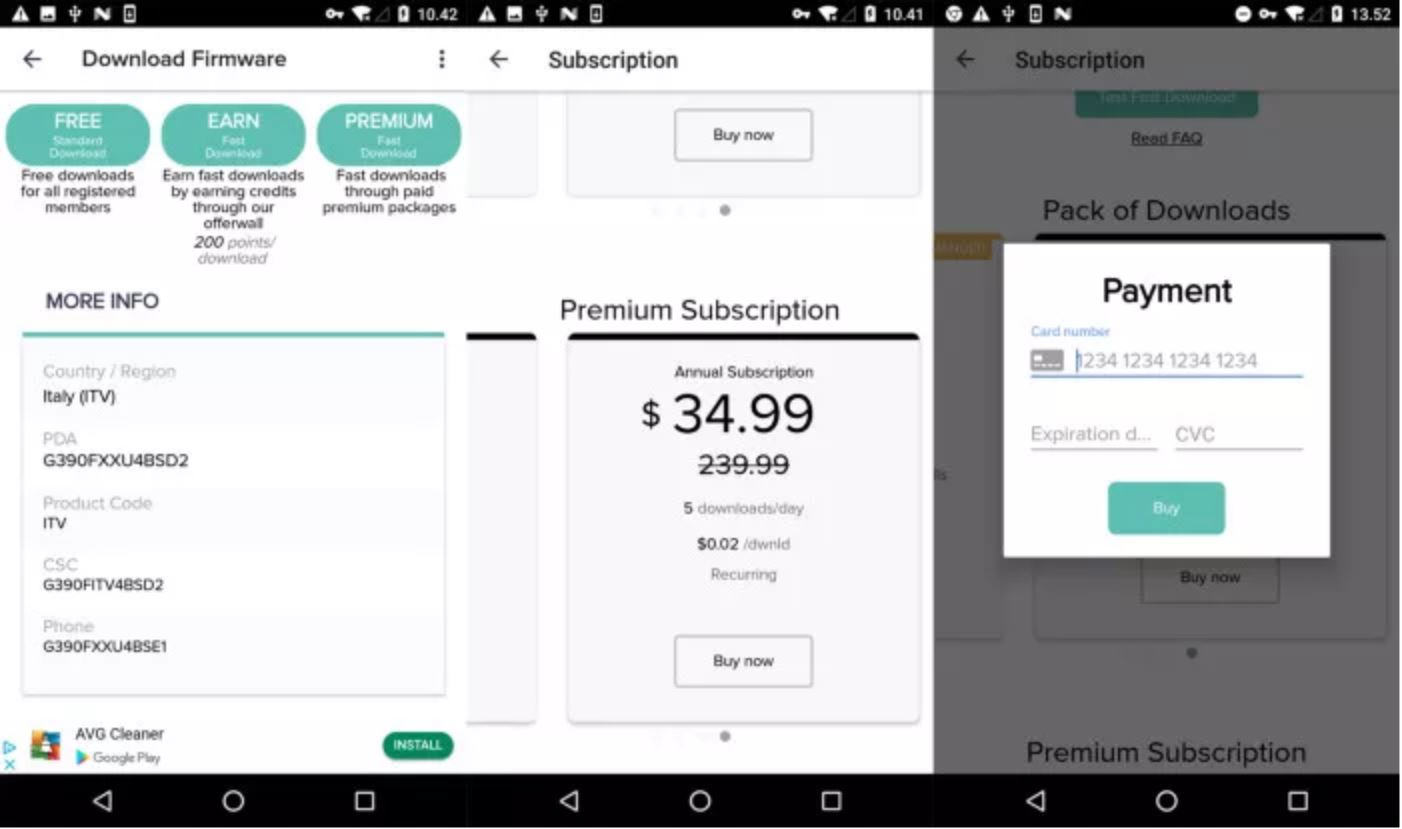
Installing a firmware/update-manager for your phone helps to ensure your phone is secure. However, for 10 million Samsung smartphone users, this has become the complete opposite. Aleksejs Kuprins, a malware analyst at CSIS Security Group, revealed how an app called “Updates for Samsung” has been installed by over 10 million users directly from the Google Play Store. The app promises free firmware updates but redirects users to an ad-filled website and asks for money to install the updates. This $34.99/year service, which is supposed to be free, doesn’t use the Google Play Store to manage the subscription. Instead, it uses a separate payment processing system to pay the fee. The download speed is also restricted to 56 Kbps and asks users pay more money for faster speeds or premium packages. Kuprins also noted that free downloads almost always failed to complete. Overall, the app is not doing what it’s advertising to do.
So, what should you do? If you have this app installed, it’s recommended to remove it from your phone as well as dispute any transactions if you paid for the service. Additional advice would be not to download apps like this going forward. Instead, follow Samsung’s procedures for downloading updates, which appear as a notification and walk you through the simple, speedy, and secure process for updating your phone. If you want to check on the status of your device’s firmware, simply navigate to the “Software Update” option in the settings menu and select “Download and install” to check if you are running the latest updates; if not, then the download will start and the update will be completed in a few minutes. By following these recommendations, the updates are guaranteed to come directly from the vendor and are always free.
The Big Picture:
No business or organization is invulnerable to a cyberattack, as these incidents prove. Business and safety operations can be heavily impacted and result in the loss of millions of dollars. To better protect your business or organization, take a proactive stance about cybersecurity.
How Can Netizen Help?
Netizen ensures that security gets built-in and not bolted-on. Providing advanced solutions to protect critical IT infrastructure such as the popular “CISO-as-a-Service” wherein companies can leverage the expertise of executive-level cybersecurity professionals without having to bear the cost of employing them full time.
We also offer compliance support, vulnerability assessments, penetration testing, and more security-related services for businesses of any size and type.
Additionally, Netizen offers an automated and affordable assessment tool that continuously scans systems, websites, applications, and networks to uncover issues. Vulnerability data is then securely analyzed and presented through an easy-to-interpret dashboard to yield actionable risk and compliance information for audiences ranging from IT professionals to executive managers.
Netizen is an ISO 27001:2013 (Information Security Management) certified company. We are a proud Service-Disabled Veteran-Owned Small Business that is recognized by the U.S. Department of Labor for hiring and retention of military veterans.



Copyright © 2019 Netizen Corporation. All rights reserved.


