
Overview
- Phish Tale of the Week
- Colonial Pipeline Didn’t have MFA in Place, Neither Do Most Defense Contractors
- US Defense Contractors Fail to Meet CMMC Requirements
- How can Netizen help?
Phish Tale of the Week
Phishing attempts can often target specific groups that can be exploited by malicious actors. In this instance, we see a phishing scam targeting unsuspecting employees that may be expecting an invoice to be paid or just someone who doesn’t check their email rigorously. This email appears to be a notice of payment confirmation for undisclosed services. This email contains an Excel file, likely with our payment information in there awaiting confirmation so why not click on the document and see for ourselves. Unfortunately, there’s plenty or reasons not to click that email right away.
Take a look below:
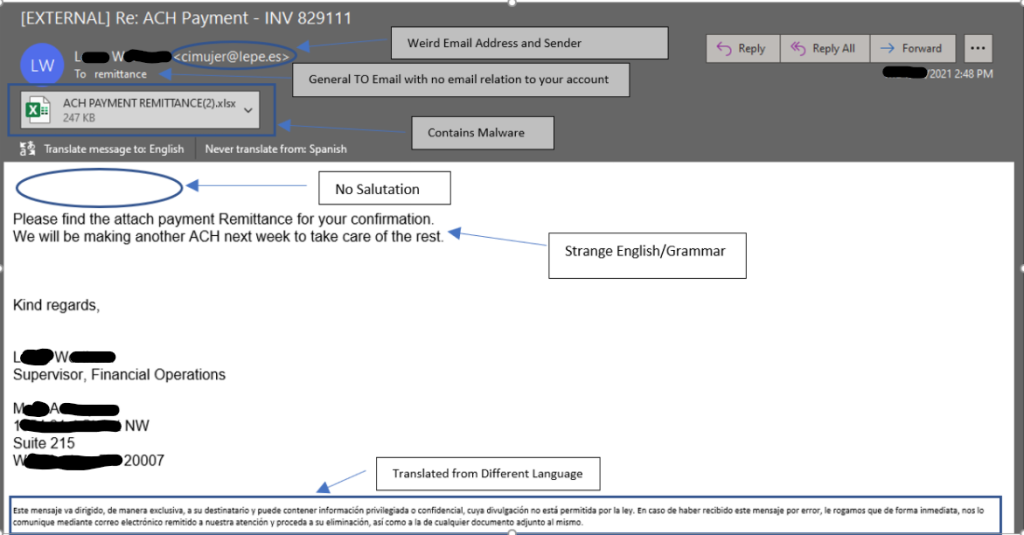
- The first red flag on this email is the sender address. Always thoroughly inspect the sender address to ensure its from a trusted sender. In the future, check all suspicious emails from companies against previous correspondences you’ve received and make sure the sender address is the same.
- The second warning sign in this email is the lack of a salutation. In most email correspondences it is customary to begin with a small opening such as “hello” or “good morning”. This email likes an attempt at an introduction and immediately jumps right to the document.
- The final warning sign for this email is the messaging inside the email. In this instance, this email was translated from another language prior to this screen grab. If an email is coming from an unknown sender, in a different language, then there is always room for concern.
General Recommendations:
A phishing email will typically direct the user to click on a link where they will then be prompted to update personal information, such as a password, credit card, social security, or bank account information. A legitimate company already has this sensitive information and would not ask for it again, especially via email.
- Scrutinize your emails before clicking anything. Have you ordered anything recently? Does this order number match the one I already have? Did the email come from a store you don’t usually order supplies from or a service you don’t use? If so, it’s probably a phishing attempt.
- Verify that the sender is actually from the company sending the message.
- Did you receive a message or email from someone you don’t recognize? Are they asking you to sign into a website to give Personally Identifiable Information (PII) such as credit card numbers, social security number, etc. A legitimate company will never ask for PII via instant message or email.
- Do not give out personal or company information over the internet.
- Do not click on unrecognized links or attachments. If you do proceed, verify that the URL is the correct one for the company/service and it has the proper security in place, such as HTTPS.
Many phishing emails pose a sense of urgency or even aggressiveness to prompt a form of intimidation. Any email requesting immediate action should be vetted thoroughly to determine whether or not it is a scam. Also, beware of messages that seek to tempt users into opening an attachment or visiting a link. For example, an attachment titled “Fix your account now” may draw the question “What is wrong with my account?” and prompt you to click a suspicious link.
Cybersecurity Brief
In this week’s Cybersecurity Brief:
Colonial Pipeline Didn’t have MFA in Place, Neither Do Most Defense Contractors

Following the massive Colonial Pipeline hack that saw gas prices surge across the country and many residents in the Southeast of the United States without gas altogether, Colonial’s CEO Joseph Blount was called to answer numerous questions from Congress. Rep. John Katko of NY appreciated that Colonial Pipeline had identified places within their environment to strengthen their security policies and further harden systems, but the question remains. “If your pipeline provides fuel to 45% of the East Coast, why are you only hardening systems after an attack?” U.S Rep. Bonnie Watson Coleman from New Jersey had a more direct response to Blount’s testimony. She went on the offensive claiming that by delaying voluntary reviews and assessments of cybersecurity policy, Colonial was declining them, not complying with them.
While companies of all sizes and security complexities can fall victim to cyberattacks such as the one Colonial Pipeline suffered, many basic precautions should be in place to prevent these sorts of disasters. One of the most basic preventative measures organizations can deploy across their networks is multifactor authentication. Multifactor Authentication or MFA for short is an authentication method that requires a user to provide two forms of evidence proving they are who they claim to be and that they are accessing systems or information that are within their security privileges. Unfortunately, Colonial Pipeline did not have MFA implemented in their environment at the time of the attack.
Experts believe MFA wouldn’t have stopped this attack in its entirety, but this disregard of basic security tools is concerning. Companies in the federal defense supply chain have been required to have multifactor authentication in place for a few years now after a 2015 law passed mandating NIST cybersecurity best practices. A CyberSheath report found that 71% of the 600 defense contractors surveyed failed to have the appropriate level of multifactor authentication needed. What’s even more concerning is that isn’t the only issue plaguing members of the defense supply chain. The Supplier Performance Risk System scores companies based off their overall risk profile in accordance with what security measures they have enacted within their environments. A company with a perfect score would be awarded a 110 on this scale while a company with no measures in place would score a -203. The average score of the 600 companies surveyed was an alarmingly low -125.
In conclusion, while federal cybersecurity requirements have been modified and improved over the years, there is still room for improvement. Many contractors have forgone these security upgrades because there hasn’t been any recourse to their actions thus far. The time for verification is now. The federal government must verify that defense contractors are following these basic cybersecurity standards and better securing the defense supply chain.
To read more about this article, click here.
US Defense Contractors Fail to Meet CMMC Requirements

A recent uptick in cyberattacks has created more than a few headaches for United States defense contractors. President Biden signed an executive order in May which signaled the first major shot in the ongoing war against outside threat actors. However, a report from incident response firm BlueVoyant illustrated that shot may have fallen on deaf ears. The survey polled 300 small to medium sized defense contractors and uncovered that many of them are currently failing to comply with CMMC requirements. The report gets worse from there with 48% of these businesses having “severe vulnerabilities” within their environments like unsecured data storage or ports and almost 10% showing “critical vulnerabilities” and indicators of compromise. In what might be the most alarming statistic from this report, 28% of the companies surveyed would not meet CMMC tier-1 requirements which mostly entail just basic cyber hygiene practices.
The report from BlueVoyant highlights some of the struggles that small and medium sized defense contractors are currently facing. These organizations are some of the first points of attack for outside threat actors looking to gain a greater foothold into the United States’ defense supply chain. Many attackers target businesses of this size since they usually allocate less money for security in their annual budgets, although the industry in which these companies are classified under may tell a different story.
Of the companies polled in this survey, Manufacturing and R&D companies were found to be at a significantly greater risk than many other companies with similar staff sizes. The report disclosed that small manufacturing businesses had the highest levels of critical risk at 14%, with 100% of large R&D companies assessed at “high risk” with countless vulnerabilities within their networks. Increasingly concerning, almost 1/3 of the R&D firms surveyed displayed indicators of compromise throughout their networks.
This report comes as defense contractors have begun the painstakingly slow process of adopting the Cybersecurity Maturity Model Certification (CMMC) requirements. This standard builds upon previous cybersecurity defense measures highlighted in NIST SP 800-171 and looks to better secure the nation’s defense supply chain. For companies looking to begin their CMMC endeavors, there are five tiers of requirements ranging from the lowest Tier 1 up to Tier 5. These tiers are broken down by the level of access companies have to sensitive information. The requirements in Tier 1 are even less intensive than previous standards from NIST SP 800-171 which further indicates the organizational failure to meet basic cybersecurity standards throughout the defense supply chain. The hard-truth is many of these companies struggle to address cybersecurity needs within their organizations. They often have limited IT resources and view the investment into better security practices as a costly one. This is why firms need to partner with organizations to help streamline their security improvements and CMMC readiness. At Netizen, our company will work one on with you to address your company’s unique security requirements and work to establish standards and practices that ensure continued compliance and security.
For more information check out the rest of the article here.
How Can Netizen Help?
Netizen ensures that security gets built-in and not bolted-on. Providing advanced solutions to protect critical IT infrastructure such as the popular “CISO-as-a-Service” wherein companies can leverage the expertise of executive-level cybersecurity professionals without having to bear the cost of employing them full time.
We also offer compliance support, vulnerability assessments, penetration testing, and more security-related services for businesses of any size and type.
Additionally, Netizen offers an automated and affordable assessment tool that continuously scans systems, websites, applications, and networks to uncover issues. Vulnerability data is then securely analyzed and presented through an easy-to-interpret dashboard to yield actionable risk and compliance information for audiences ranging from IT professionals to executive managers.
Netizen is an ISO 27001:2013 (Information Security Management) certified company. We are a proud Service-Disabled Veteran-Owned Small Business that is recognized by the U.S. Department of Labor for hiring and retention of military veterans.


