
Overview
- Phish Tale of the Week
- Chinese State-Sponsored Hackers Compromise Multiple U.S State Governments
- Altoona Area School District Affected By Cyberattack
- How can Netizen help?
Phish Tale of the Week
Phishing attempts can often target specific groups that can be exploited by malicious actors. In this instance, we see a phishing scam targeting unsuspecting McAfee customers. This email appears to be a notification alerting us that our computer is no longer protected and our subscription has expired. We are then prompted to renew our subscription and activate the code below now. This email contains a convincing message saying to protect my device from hackers, so why not click the link and update details? Unfortunately, there are plenty of reasons not to click that email right away.
Take a look below:
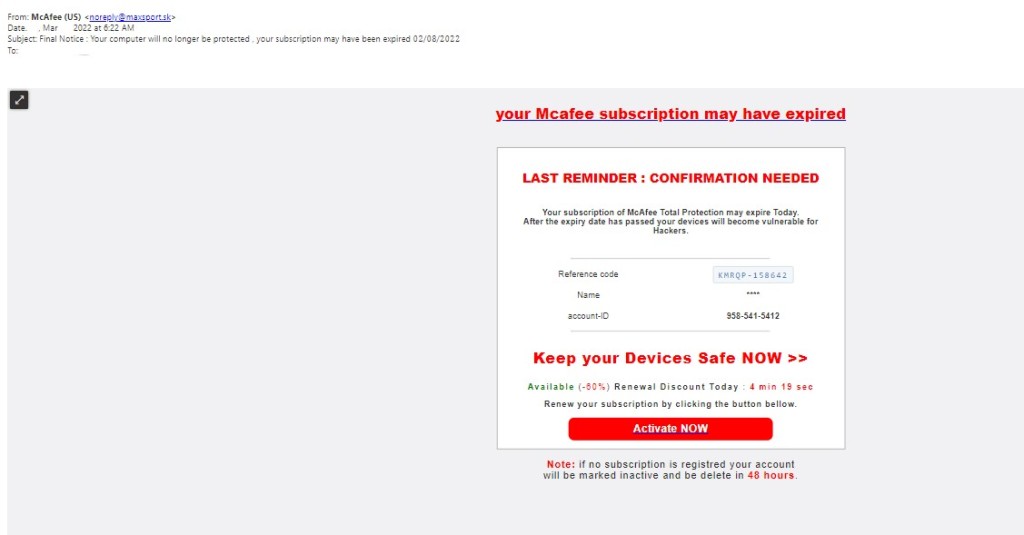
- The first red flag on this email is the sender address. Always thoroughly inspect the sender address to ensure its from a trusted sender. In the future, review the sender address thoroughly to see if the email could be coming from a threat actor.
- The second warning sign in this email is the urgency created in the message. The subject line tells us that “our computer is no longer protected” and further reads “Keep your Devices Safe NOW”. This type of messages is commonly used by threat actors to elicit an urgent and fast reply out of their target.
- The final warning sign for this email is the large red “Activate NOW” call to action. Threat actors use call to action buttons like this to immediately redirect targets to malicious landing pages. These landing pages then infect the targets system with malware or other software with the intention of stealing information or further exortion.
General Recommendations:
A phishing email will typically direct the user to click on a link where they will then be prompted to update personal information, such as a password, credit card, social security, or bank account information. A legitimate company already has this sensitive information and would not ask for it again, especially via email.
- Scrutinize your emails before clicking anything. Have you ordered anything recently? Does this order number match the one I already have? Did the email come from a store you don’t usually order supplies from or a service you don’t use? If so, it’s probably a phishing attempt.
- Verify that the sender is actually from the company sending the message.
- Did you receive a message or email from someone you don’t recognize? Are they asking you to sign into a website to give Personally Identifiable Information (PII) such as credit card numbers, social security number, etc. A legitimate company will never ask for PII via instant message or email.
- Do not give out personal or company information over the internet.
- Do not click on unrecognized links or attachments. If you do proceed, verify that the URL is the correct one for the company/service and it has the proper security in place, such as HTTPS.
Many phishing emails pose a sense of urgency or even aggressiveness to prompt a form of intimidation. Any email requesting immediate action should be vetted thoroughly to determine whether or not it is a scam. Also, beware of messages that seek to tempt users into opening an attachment or visiting a link. For example, an attachment titled “Fix your account now” may draw the question “What is wrong with my account?” and prompt you to click a suspicious link.
Cybersecurity Brief
In this week’s Cybersecurity Brief:
Chinese State-Sponsored Hackers Compromise Multiple U.S State Governments

Investigators from the cybersecurity firm Madiant have uncovered a Chinese state-sponsored hacking group that compromised at least six U.S state governments. The persistent attacks took place between May 2021 and February 2022. The group, identified as APT41, used web application vulnerabilities to gain their initial foothold into multiple state governments. Additionally, Mandiant has found that APT41 exfiltrated personally identifiable information (PII) from the affected systems in manners similar to recorded previous espionage operations but has yet to confirm whether this was an intelligence-gathering operation the Chinese government.
“APT41′s recent activity against U.S state governments consists of significant new capabilities, from new attack vectors to post-compromise tools and techniques. APT41 can quickly adapt their initial access techniques by re-compromising an environment through a different vector, or by rapidly operationalizing a fresh vulnerability.” a researcher from Mandiant added.
Microsoft is one of the most prominent tech manufacturers globally, and attacks like this have become the new normal for this U.S.-based company. Reports of a 2.4 terabit per second (tbps) attack in October 2021 and two other large-scale DDoS attacks, each with 2.5 tbps, show just how many times Microsoft’s Azure DDoS protection Team has to put their skills to the test.
This attack marks another instance where nation-state hackers from China were able to infiltrate U.S state systems and remain undetected for months on end. These threat actors utilized numerous tools and techniques to adapt to any defenses that may have begun to uncover their trail. This shows a persistence and long-term focused resolve that many inside the U.S. government were afraid would show in attacks from nation-state hackers.
Following the initial report on this attack, a spokesperson for the Cybersecurity and Infrastructure Security Agency (CISA) stated they were aware of the breach and had this to add:
“CISA is actively working with our JCDC [Joint Cyber Defense Collaborative] private sector partners, including Mandiant, and government partners to address this advanced persistent threat to state government agencies and assist impacted entities. We encourage all organizations and critical infrastructure entities impacted by cyber intrusions to report to CISA, and to visit CISA.gov to take action to protect themselves.”
According to Mandiant’s researchers, members of APT41 were able to initially compromise U.S state government networks by exploiting vulnerabilities in applications built with Microsoft’s .NET platform. One of the vulnerabilities exploited was previously unknown and was found in an animal health reporting database system called USAHERDS. Experts believe the extent of this attack is going to be much larger than previously reported, with almost 20 different state governments reporting use of USAHERDS in their facilities.
U.S government officials were pressed on the motive of APT41’s most recent attack earlier this week and believe their focus was an espionage reconnaissance mission to determine the response of U.S state governments. When asked for a response, Zhao Lijin, a spokesperson for China’s foreign ministry stated:
“China firmly opposes and combats any form of cyberattacks and will not encourage, support, or condone any cyberattacks.”
To read more about this article, click here.
Altoona Area School District Affected By Cyberattack

Earlier this week, the Altoona Area School District sent a letter out to faculty and staff alerting them that a cyberattack affecting their internal systems had occurred. School superintendent Charles Prijatelj stated: “Altoona Area School District recently discovered it was the victim of a sophisticated cybersecurity incident, which impacted certain internal systems. Upon discovery of the incident, our IT took several steps to contain the incident and third-party forensic advisors and external legal counsel were engaged to assist”.
News publications around Altoona received numerous anonymous phone calls describing the effects of the cyberattack, with many teachers reporting that their credit card agencies alerted them that their personal information was now found on the dark web. Researchers investigating the incident believe that social security numbers, full names, addresses, insurance id numbers, and staff telephone numbers were all compromised in this breach. Prijatelj later commented on the incident, further exclaiming that Altoona’s IT department was in the process of containing the incident and has engaged third-party forensic investigators to assist with remediation.
Cyberattacks have become more frequent across the country as threat actors have found a new lucrative target to exploit. Schools districts house troves of personally identifiable information for both students and faculty alike. This, coupled with abysmal amounts of funding for security-related projects, creates the perfect storm for threat actors looking for a quick payout. The public nature of these institutions also means that when a breach occurs or ransomware is detected, the schools almost always have to agree to the hackers’ demand and pay the ransom.
Superintendent Charles Prijatelj penned a separate letter to parents and guardians of children in the school district, saying: “We do know that some of our employees have received notification of potential data compromise and we wanted to make you aware of the situation as well. Upon completion of the investigation, those individuals with compromised data will receive official notification. At this time, however, that information is not yet known.” Prijatelj then thanked parents for their patience and assured them that more information will be made available as the district uncovers more about this incident.
For more information check out the rest of the article here.
How Can Netizen Help?
Netizen ensures that security gets built-in and not bolted-on. Providing advanced solutions to protect critical IT infrastructure such as the popular “CISO-as-a-Service” wherein companies can leverage the expertise of executive-level cybersecurity professionals without having to bear the cost of employing them full time.
We also offer compliance support, vulnerability assessments, penetration testing, and more security-related services for businesses of any size and type.
Additionally, Netizen offers an automated and affordable assessment tool that continuously scans systems, websites, applications, and networks to uncover issues. Vulnerability data is then securely analyzed and presented through an easy-to-interpret dashboard to yield actionable risk and compliance information for audiences ranging from IT professionals to executive managers.
Netizen is a CMMI V2.0 Level 3, ISO 9001:2015, and ISO 27001:2013 (Information Security Management) certified company. We are a proud Service-Disabled Veteran-Owned Small Business that is recognized by the U.S. Department of Labor for hiring and retention of military veterans.


