The Cybersecurity Maturity Model Certification (CMMC) 2.0 is a certification program developed by the U.S. Department of Defense (DoD) to assess the cybersecurity practices of contractors who handle Federal Contract Information (FCI) and Controlled Unclassified Information (CUI). The program aims to protect sensitive government information and ensure that contractors handling this information have appropriate cybersecurity measures.
The CMMC 2.0 model consists of multiple levels, ranging from basic cybersecurity hygiene to advanced threat detection and response capabilities, and includes 17 domains of cybersecurity practice. To be certified, contractors will either self-assess for Level 1 or undergo a third-party assessment and demonstrate compliance with the relevant CMMC 2.0 requirements for Levels 2 and 3. This program is mandatory for all DoD contractors and is designed to be a continuous process, with regular assessments to ensure that contractors maintain their certification and stay up-to-date with the latest cybersecurity best practices.
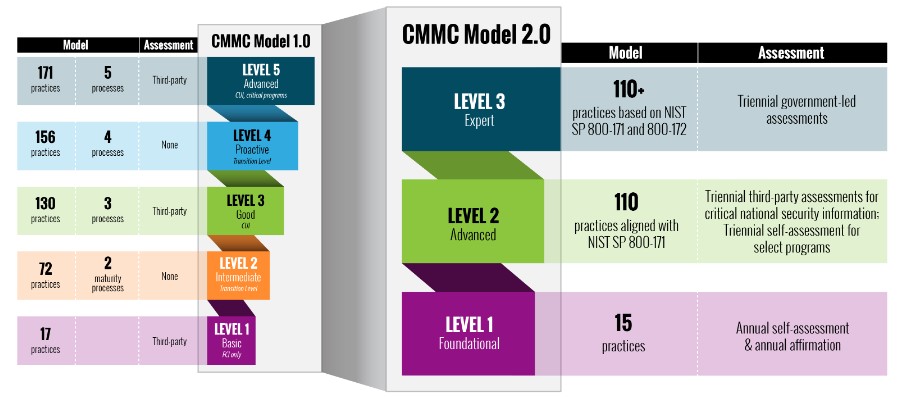
What are the 3 levels of CMMC 2.0?
The CMMC 2.0 framework is broken down into 3 different levels ranging from basic cyber hygiene to adhereing with advance information security controls outlined in NIST Special Publication 800-172.
- Level 1: Foundational Security. Basic safeguarding of Federal Contracting Information (FCI) in FAR Clause 52.204-21, 17 practices
- Level 2: Advanced Security. Aligns with the 110 controls and security requirements of NIST 800-171.
- Level 3: Expert Security. Focsued on the reduction of Advanced Persistent Threats (APTs). Controls will align with requirements laid out in NIST SP 800-172.
Companies can take the following steps to prepare for the Cybersecurity Maturity Model Certification 2.0 (CMMC) process:
- Assess current cybersecurity posture, review CMMC 2.0 controls for applicable level, and identify any gaps in compliance with the CMMC requirements. Organizations that first prioritize understanding the CMMC 2.0 requirements their will need to meet will immediately put themselves on the right path.
- Develop a plan to address any identified gaps, including a timeline for implementation. Setting attainable targets for compliance will help reduce the stress and burden that comes with meeting CMMC 2.0 requirements.
- Train employees on cybersecurity best practices, including how to identify and report potential threats.
- Implement technical controls, such as firewalls, antivirus software, and intrusion detection systems, to safeguard their networks and systems.
- Develop incident response and business continuity plans to prepare for and respond to potential security breaches.
- Regularly monitor and audit their systems and networks to ensure they comply with the CMMC 2.0 requirements and detect and respond to any potential threats.
- Lastly, consider hiring a third-party assessor to conduct an assessment, help identify vulnerabilities, and ensure compliance with the CMMC 2.0 standards. Third-party assessors are a great resource to help prioritize which controls your organization should focus on, as well as updating applicable documentation to meet CMMC 2.0 standards.
Conclusion:
Overall, CMMC 2.0 can seem like a daunting framework for any company to tackle. These compliance requirements were created with information security best practices as the foundation. Companies that have been adhereing to industry best standards will have little trouble configuring their environments to meet compliance. Even firms that have not been heavily investing into their cybersecurity posture can still achieve CMMC 2.0 compliance with proper preparation, an understanding of the controls, and a well thought out timeline to remediate any gaps in compliance.
How Can Netizen Help?
Netizen ensures that security gets built-in and not bolted-on. Providing advanced solutions to protect critical IT infrastructure such as the popular “CISO-as-a-Service” wherein companies can leverage the expertise of executive-level cybersecurity professionals without having to bear the cost of employing them full time.
We also offer compliance support, vulnerability assessments, penetration testing, and more security-related services for businesses of any size and type.
Additionally, Netizen offers an automated and affordable assessment tool that continuously scans systems, websites, applications, and networks to uncover issues. Vulnerability data is then securely analyzed and presented through an easy-to-interpret dashboard to yield actionable risk and compliance information for audiences ranging from IT professionals to executive managers.
Netizen is an ISO 27001:2013 (Information Security Management), ISO 9001:2015, and CMMI V 2.0 Level 3 certified company. We are a proud Service-Disabled Veteran-Owned Small Business that is recognized by the U.S. Department of Labor for hiring and retention of military veterans.
Questions or concerns? Feel free to reach out to us any time – https://www.netizen.net/contact