Overview:
- Phish Tale of the Week
- LVHN Suffers Ransomware Attack by Russian Cyber Gang
- CISA Director Calls for Increased Accountability in Application/Hardware Development
- How can Netizen help?
Phish Tale of the Week
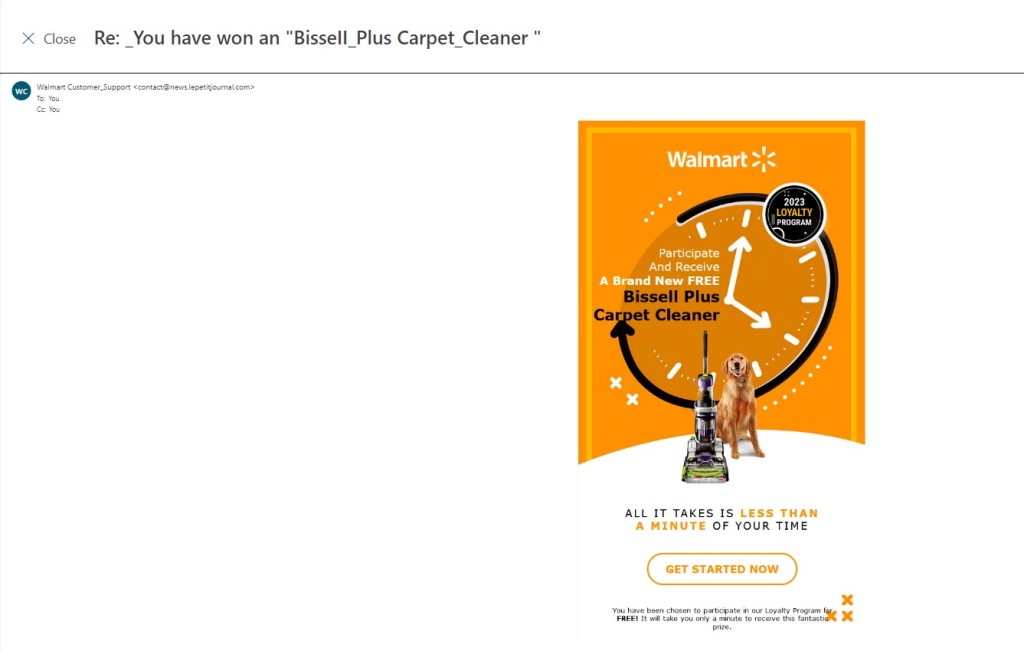
Phishing attempts can often target specific groups that can be exploited by malicious actors and come in many different forms. In this instance, we see a phishing scam targeting Walmart customers with what appears to be a link to a loyalty survey. Once we complete the loyalty survey we are told we will receive a “Brand New FREE Bissell Plus Carpet Cleaner”. This survey apparently only takes a minute of our time, so why shouldn’t we click on the “Get Started Now” button? Fortunatently for us, there are plenty of signs that this email is a phishing scam.
Here’s how we know not to click on either of this link:
- The first red flags in this message is the senders’ addresses. Always thoroughly inspect the sender’s address to ensure it’s from a trusted sender. In this case, the message comes from an email address we are unfamiliar with. In the future, review the sender’s address thoroughly to see if the email could be coming from a threat actor.
- The second warning signs in this email is the messaging. This message tries to elicit a response by offering a free prize incentive for completing their loyalty survey. Phishing scams commonly use prizes and promises of free gifts to elicit an immediate response from their targets. Always be sure to thoroughly inspect the messaging of all emails in your inbox.
- The final warning sign for this email is the lack of legitimate Walmart information. Fortune 500 companies and similar organizations standardize all email communications with customers. Support links, addresses, acceptable use policies, and other information is always provided at the bottom of each email, along with options to unsubscribe or change messaging preferences. This email lacks all signs of a credible Walmart email and can be immediately detected as a phishing attempt.
General Recommendations:
A phishing email will typically direct the user to click on a link where they will then be prompted to update personal information, such as a password, credit card, social security, or bank account information. A legitimate company already has this sensitive information and would not ask for it again, especially via email.
- Scrutinize your emails before clicking anything. Have you ordered anything recently? Does this order number match the one I already have? Did the email come from a store you don’t usually order supplies from or a service you don’t use? If so, it’s probably a phishing attempt.
- Verify that the sender is actually from the company sending the message.
- Did you receive a message or email from someone you don’t recognize? Are they asking you to sign into a website to give Personally Identifiable Information (PII) such as credit card numbers, social security number, etc. A legitimate company will never ask for PII via instant message or email.
- Do not give out personal or company information over the internet.
- Do not click on unrecognized links or attachments. If you do proceed, verify that the URL is the correct one for the company/service and it has the proper security in place, such as HTTPS.
Many phishing emails pose a sense of urgency or even aggressiveness to prompt a form of intimidation. Any email requesting immediate action should be vetted thoroughly to determine whether or not it is a scam. Also, beware of messages that seek to tempt users into opening an attachment or visiting a link. For example, an attachment titled “Fix your account now” may draw the question “What is wrong with my account?” and prompt you to click a suspicious link.
Cybersecurity Brief
In this week’s Cybersecurity Brief:
LVHN Suffers Ransomware Attack by Russian Cyber Gang

The Lehigh Valley Health Network (LVHN) was hit by a suspected ransomware attack earlier this month. On Monday, February 20th, 2023, LVHN CEO and President Brian Nester commented, “Lehigh Valley Health Network has been the target of a cybersecurity attack by a ransomware gang, known as BlackCat, which has been associated with Russia. As of today, the attack has not disrupted LVHN’s operations. Based on our initial analysis, the attack was on the network supporting one physician practice located in Lackawanna County. We take this very seriously and protecting the data security and privacy of our patients, physicians and staff is critical.”
Reports from inside LVHN indicated that the initial breach targeted an LVHN subsidiary Delta Medix in Lackawanna County, PA. From there, threat actors were able to pivot across the network and expand their ransomware payload to multiple locations. LVHN’s IT team was quick to contain the intrusion and has reportedly refused to pay the ransom demanded by BlackCat. Nester later added that “Although our investigation is ongoing, as of today, our initial analysis shows that the incident involved a computer system used for clinically appropriate patient images for radiation oncology treatment and other sensitive information. BlackCat demanded a ransom payment, but LVHN refused to pay this criminal enterprise. We understand that BlackCat has targeted other organizations in the academic and healthcare sectors.”
Ransomware attacks like this have surged across the United States in the last few years, with sectors like healthcare and education facing the brunt of these intrusions. Many in the information security community have urged companies to further invest in backup technology to ensure that business is only disrupted or delayed by a few hours at max in the event of a ransomware attack. However, backups will not solve the issue of ransomware altogether.
BlackCat and other ransomware gangs often rely on human error to break into different organizations. Clicking on a bad email link or unknowingly inserting a malicious USB drive into a laptop could prove disastrous for any company’s IT security posture. Organizations must change how security is taught to employees and expand on continuous cybersecurity training for all staff. Employees that are exposed to threat actor attack methods like phishing scams and social engineering tactics are far more likely to scrutinize potential threats in the future and report them to their IT teams.
This is not the first time LVHN has suffered a cybersecurity incident. In 2021, LHVN sustained a major PII breach when a third-party file transfer service was hacked, exposing patient information such as DOB, address, social security numbers, and more.
“We are continuing to work closely with our cybersecurity experts to evaluate the information involved and will provide notices to individuals as required as soon as possible. Attacks like this are reprehensible and we are dedicating appropriate resources to respond to this incident.” said LVHN CEO Brian Nester when discussing LVHN’s response to the ransomware attack.
In conclusion, ransomware attacks like this are on the rise globally and will continue to single out sectors such as healthcare and education. Organizations must improve their security training for all staff immediately. Cultures centered around security and a cautious approach to potential IT threats will serve firms well in the long run.
To read more about this article, click here.
CISA Director Calls for Increased Accountability in Application/Hardware Development

Software companies have focused on building applications quickly for far too long, with functionality as the main priority. Numerous firms have come under fire recently for having their applications exploited in ransomware attacks and other cyber intrusions. The Director of the Homeland Security Cybersecurity and Infrastructure Security Agency (CISA), Jen Easterly, directed private corporations to bring security to the top of the discussion for application development. The CISA director even went as far as to suggest that corporations that continue to build applications insecurely may face fines and penalties if their software is leveraged for a cyberattack.
“Congress should advance legislation allowing software manufacturers to be held legally liable for the insecurity of their products, and it should also shield companies that develop secure software from legal liability.” This statement by Easterly on Monday follows a renewed push by CISA to convince private companies to build secure applications from the ground up rather than try to bolt on or in many cases place “cybersecurity tape” over gaping holes in their applications. Easterly later added, “Government can work to advance legislation to prevent technology manufacturers from disclaiming liability by contract, establishing higher standards of care for software in specific critical infrastructure entities and driving the development of a safe harbor framework to shield from liability companies that securely develop and maintain their software products and services.”
This legislation would shift the liability of security from the end-user to the manufacturing corporation. Users often accept liability and terms of service agreements when unpackaging new tech hardware or software online. Few people actually read these policies in their entirety and unknowingly accept ludicrous liability policies that place the burden of security on the user rather than the corporation developing the product.
At the same time, legislation like this would assure companies that take the necessary steps to securely develop applications/hardware would not be penalized if a sophisticated threat actor was able to breach their systems. This “safe harbor” would set acceptable guidelines for companies to develop new applications or hardware. This way, companies that ultimately do end up getting breached will not face the full brunt of public scrutiny and penalties as long as they follow best practices set by CISA.
Overall what Jen Easterly is trying to champion is a worthy cause in practice. However, original proponents of this fight date back to 2002, with many saying that special interest groups and tech start-ups everywhere will fight legislation like this tooth and nail. Putting a new focus on security in applications and hardware will result in more labor costs and longer production cycles, which will ultimately be a net negative for shareholder value. Although, more secure products will reduce the likelihood of a breach and potential negative impact caused by similar cyber intrusions. It remains to be seen whether or not lawmakers will heed the advice of CISA’s director and increase cybersecurity accountability for software companies.
For more information, check out the rest of the article here.
How Can Netizen Help?
Netizen ensures that security gets built-in and not bolted-on. Providing advanced solutions to protect critical IT infrastructure such as the popular “CISO-as-a-Service” wherein companies can leverage the expertise of executive-level cybersecurity professionals without having to bear the cost of employing them full time.
We also offer compliance support, vulnerability assessments, penetration testing, and more security-related services for businesses of any size and type.
Additionally, Netizen offers an automated and affordable assessment tool that continuously scans systems, websites, applications, and networks to uncover issues. Vulnerability data is then securely analyzed and presented through an easy-to-interpret dashboard to yield actionable risk and compliance information for audiences ranging from IT professionals to executive managers.
Netizen is a CMMI V2.0 Level 3, ISO 9001:2015, and ISO 27001:2013 (Information Security Management) certified company. We are a proud Service-Disabled Veteran-Owned Small Business that is recognized by the U.S. Department of Labor for hiring and retention of military veterans.