Penetration testing is an invaluable skill in the toolbox of a cybersecurity analyst, a skill that is much more open ended than other day-to-day tasks on an analyst’s daily agenda. With this open-endedness comes a degree of freedom in how red-teamers go about performing these pentests, leading to a variety of approaches that different penetration testers are able to take.
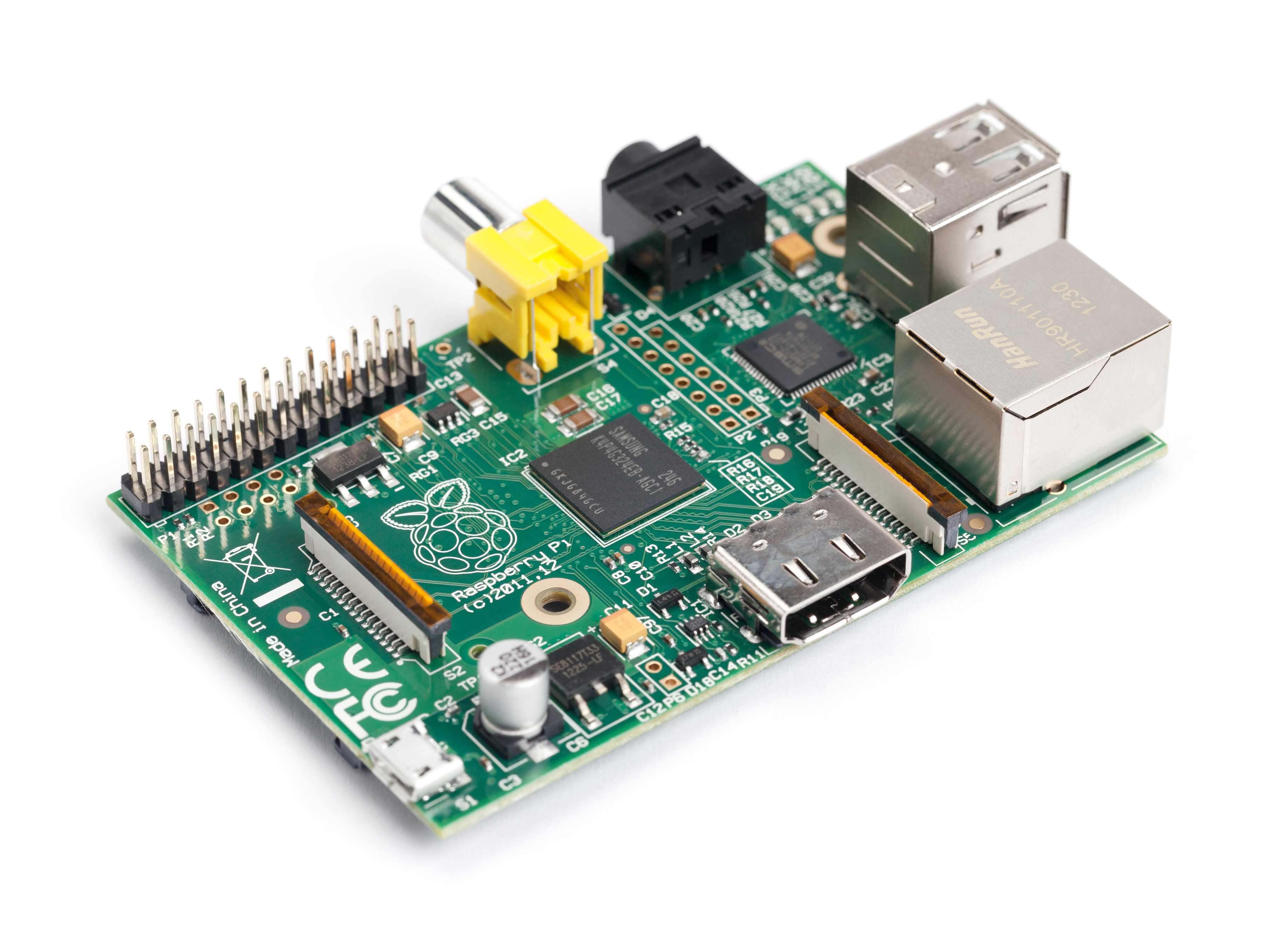
One tool I’ve personally found invaluable during internal penetration tests is a drop box—a compact device that allows remote access to internal networks for security assessments. While many pre-built options are available, creating a custom dropbox using a Raspberry Pi 3, a TP-Link AC1300 Wi-Fi adapter, and a 32GB SD card, like we have, offers a cost-effective and secure alternative.
In this guide, I’ll walk you through building your own drop box, tailored to support internal network testing, Wi-Fi audits, and secure VPN access via OpenVPN.
What is a Drop Box?
A drop box is a small, portable device used for penetration testing on internal networks. These tools allow cybersecurity teams to access client environments remotely, conducting thorough network assessments from any location. Popular devices from vendors such as Hak5 offer similar functionality, but building your own allows for greater customization and lower costs.
At Netizen, we’ve developed our own dropbox, designed to be cost-effective, secure, and easy to deploy. Whether for network security testing or Wi-Fi auditing, this device helps ensure we maintain secure and efficient workflows without needing an on-site presence.
Here’s a revised guide for building a penetration testing dropbox using a Raspberry Pi 3, a TP-Link AC1300 Wi-Fi adapter, a 32 GB SD card, Rufus for etching, and OpenVPN for remote access. Creating a drop box for penetration testing with different hardware/software is easily achievable, as long as the replacement achieves the same function.
Requirements
For our build, we have a few key requirements:
- Secure by Default: The device must be secure to avoid introducing new vulnerabilities to the client.
- Cost-Effective: The components must be affordable and replaceable.
- Easy to Deploy: Clients should be able to plug in the device without any complex setup.
- Wi-Fi Support: The device needs to support Wi-Fi auditing tools for comprehensive assessments.
Hardware Components
For this setup, we’ve opted for the following:
- Raspberry Pi 3: Provides enough power for the required tasks, at a lower cost compared to newer models.
- 32 GB MicroSD Card: Sufficient storage for the OS, tools, and logs.
- TP-Link AC1300 Wi-Fi Adapter: Known for its reliability and good range, with support for monitor mode.
- Raspberry Pi Case: Choose one that accommodates the Raspberry Pi 3.
- USB Power Supply: A plug-in model is recommended for longer use, rather than a power bank.
- MicroSD Card Reader: Necessary for flashing the operating system.
- (Optional) HDMI-to-micro HDMI cable, USB keyboard, and mouse: Handy for initial setup if you don’t use a headless configuration.
Software Components
- Rufus: Use this tool to flash the operating system onto the SD card.
- Kali Linux for Raspberry Pi: This is the primary OS for the dropbox, containing the necessary tools for penetration testing.
- TP-Link AC1300 Drivers: These will ensure the Wi-Fi adapter functions correctly.
- OpenVPN: OpenVPN will provide secure remote access to the dropbox for monitoring and testing.
Setting Up the Raspberry Pi
1. Flash the OS
Start by using Rufus to flash Kali Linux onto your 32 GB SD card:
- Insert the MicroSD card into your computer and launch Rufus.
- Select the Kali Linux image and choose your MicroSD card as the target.
- Hit “Start” to flash the image onto the card.
Once this is complete, you’ll be ready to insert the card into the Raspberry Pi.
2. Initial Setup
For the initial setup, you can either connect the Raspberry Pi to a monitor, keyboard, and mouse, or access it remotely after the initial boot.
- Insert the MicroSD card into the Raspberry Pi.
- Plug in the TP-Link AC1300 Wi-Fi adapter.
- Power up the Pi and log in with the default credentials.
3. Configuring the Raspberry Pi
Once logged in, perform the following steps:
- Change the default password:
passwd - Update the system and packages:
sudo apt update && sudo apt upgrade -y - Install TP-Link AC1300 Wi-Fi adapter drivers:
You may need to download the specific drivers from the TP-Link website, then install them using the following command:
sudo apt install rtl8812au-dkms
- Install OpenVPN:
First, update the package list and install OpenVPN:
sudo apt install openvpn
Next, configure OpenVPN to secure the remote connection to your dropbox. You will need an OpenVPN configuration file, which you can create or request from your VPN provider. Here’s a link to more OpenVPN setup documentation.
- Disable unnecessary services for security:
Disable SSH to reduce potential attack vectors, as OpenVPN will handle remote access:
sudo systemctl stop ssh
sudo systemctl disable ssh
- Clear any unnecessary network configurations and sensitive information from the device.
Deploying the Dropbox
Once your dropbox is ready, deployment is straightforward:
- Insert the TP-Link AC1300 Wi-Fi adapter into the Raspberry Pi.
- Connect the Raspberry Pi to the client’s network via an Ethernet cable for internal network testing.
- Power on the Raspberry Pi using the USB power adapter.
- Connect to the dropbox remotely using OpenVPN and begin your testing.
You can now run network scans, Wi-Fi assessments, or any other penetration testing tasks using the remote connection.
Conclusion
This guide walks you through creating a customizable penetration testing drop box using a Raspberry Pi 3, TP-Link AC1300 Wi-Fi adapter, and OpenVPN for secure remote access. With this drop box, you can test internal and Wi-Fi networks remotely, giving you a flexible tool for network assessments while minimizing the need for site visits and/or other methods of network access.
How Can Netizen Help?
Netizen ensures that security gets built-in and not bolted-on. Providing advanced solutions to protect critical IT infrastructure such as the popular “CISO-as-a-Service” wherein companies can leverage the expertise of executive-level cybersecurity professionals without having to bear the cost of employing them full time.
We also offer compliance support, vulnerability assessments, penetration testing, and more security-related services for businesses of any size and type.
Additionally, Netizen offers an automated and affordable assessment tool that continuously scans systems, websites, applications, and networks to uncover issues. Vulnerability data is then securely analyzed and presented through an easy-to-interpret dashboard to yield actionable risk and compliance information for audiences ranging from IT professionals to executive managers.
Netizen is an ISO 27001:2013 (Information Security Management), ISO 9001:2015, and CMMI V 2.0 Level 3 certified company. We are a proud Service-Disabled Veteran-Owned Small Business that is recognized by the U.S. Department of Labor for hiring and retention of military veterans.
Questions or concerns? Feel free to reach out to us any time –
https://www.netizen.net/contact